TLDR, please double, triple, check your editor access permissions (details at bottom), for each app you work on.
Imagine logging into your Bubble app one day to find that someone has accessed your user data, logged in as admin users, or worse, deployed changes to your app that could exploit your users. This scenario is a real possibility for thousands of Bubble app creators right now. How do I know? I’ve just completed a security audit of over 18,000 live Bubble applications, and the results were surprising.
I’ve always believed and advocated for Bubble’s ability to democratize app development. However, this also means that thousands of apps are published where security is an afterthought. I wanted to better understand trends in the security of Bubble apps in order to help improve the platform’s security overall and ensure that Bubble can be used to its fullest extent, without compromising security.
None of these issues are a result of security issues in Bubble itself - rather, it’s poor development practice for which the responsibility lies with app developers. I’ve already communicated with Bubble to show them the process, methodology, detailed results, and provided some common-sense recommendations that would mitigate issues like these.
11.2% of live Bubble apps have public editors
I wanted to answer a simple question: how many Bubble apps have unknowingly left their editor open and vulnerable?
NB: When I talk about live Bubble apps, I mean live Bubble apps that we’ve audited (over 18,000), filtering out templates. We don’t have any reason to think it’s not representative of the ecosystem as a whole. More about methodology at the bottom.
Let’s cut to the chase:
-
11.2% of live Bubble apps have public editors - that’s more than 1 in 10 apps leaving their entire live database, backend, and app logic exposed to anyone.
-
This includes 3.3% of live Bubble apps that have fully public read and write access. This means anyone can modify your app, its data, and deploy changes to live.
A public editor permits ‘Run as’ access to Users, in both test and live databases, allowing any user to log in as one of your admin users and do whatever they’d like while logged in.
Private editors are secure. Read only editors are public, allow you to see live data and run as any user. Open editors have the same permissions as read only editors, but allow you to modify the app and deploy to live.
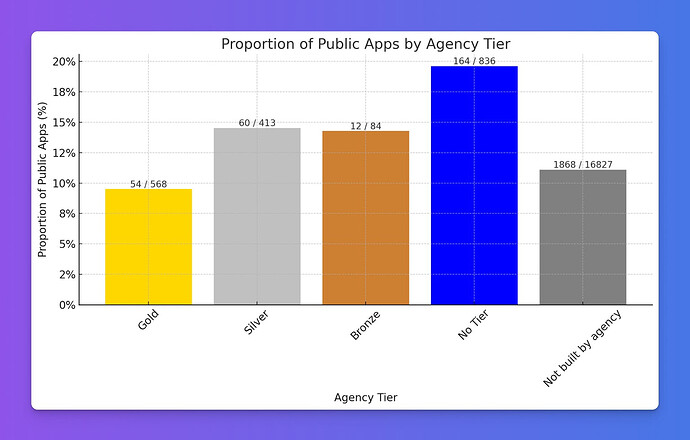
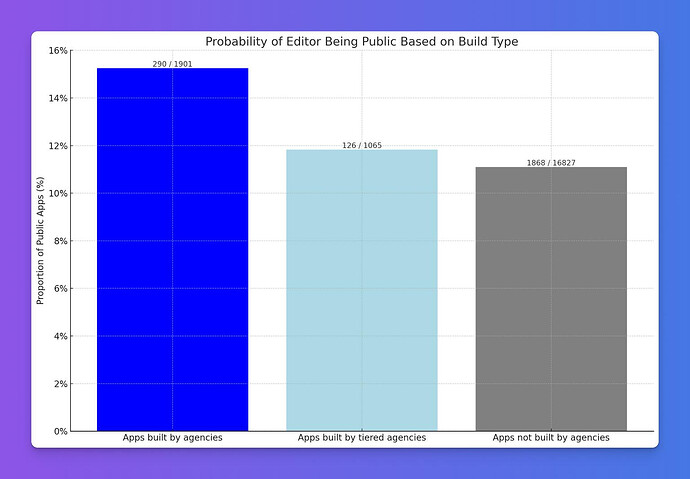
Apps built by agencies and freelancers are less secure
If you’ve hired an agency to build your Bubble app, thinking you’re in safe hands, unfortunately you’d be mistaken. Our audit revealed that agency-built apps are 37% more likely to have public editors compared to apps built by individual developers.
I’m not going to shame agencies or developers by pointing fingers publicly (though having a ranked list of agencies by % of their apps that are public is both enlightening and frightening). Instead, I want to highlight how easy it is for anyone – even professionals – to overlook critical security measures.
The proportion of live apps built by this agency tier that were found to be public
For all agencies with more than 5 apps, here’s a ranked list (colored by tier) of agencies by percentage of public apps. Higher is worse. We decided not to show the absolute numbers of apps audited for each agency as this may make them identifiable.
Gold agencies perform slightly better on average which is good news, but the fact remains: even among the “best,” nearly 1 in 10 apps is left wide open, and the Gold rate is only 1.6 percentage points better than apps not built by an agency at all.
The proportion of live apps built by this agency tier that were found to be public.
There is significant variability in security between agencies. One Gold agency even had 66% of their apps as public, yet this agency as well as multiple other significantly below-average agencies are ‘trusted partners’ for a pretty well known security platform. It goes to show that as a potential client trying to find an agency to work with in Bubble, there really is no reliable way to vet an agency’s quality and build practices if you’re not familiar with Bubble itself. I went in to detail on this topic here, so won’t go any further than this. This also links to one of the recommendations I made to Bubble, which is that agency tier awards should have at least some due diligence with respect to an agency’s quality.
Why do agencies perform worse at this security metric?
The reason isn’t certain. However, I speculate that agencies make an editor public during the project to allow people to work on it that do not have agency plans, bypassing Bubble’s collaborator limit. A common case would be where a developer asks their team for support so shares a public editor link for quick help, and forgets to private it again. There’ll be a small number of apps where the client made it public after the agency handed it over, but this is exceedingly rare and is covered further in the FAQs at the bottom of this post.
What do we do now?
We found over 2000 apps with public editors, and many more with insecure admin pages. It is not feasible for us to contact all of these individually. However, in an effort to improve the security of these apps, I’ve tried to reach out to agencies with large numbers of public apps, as well as particularly vulnerable app owners.
It’s interesting to note how different agencies responded when notified that many of their delivered apps were public. Some responded well, fixing the issues quickly, taking responsibility for it and saying they were going to review their processes to see how it could be allowed to happen. Others insisted it was a Bubble bug depsite being provided with links to their app’s editors, and ignored it.
Fortunately, as many agencies have acted upon our advice, we’ve likely been able to secure 100s of apps, preventing numerous potential data breaches and protecting thousands of end users.
There’s a challenge for Bubble, which is that Bubble is the platform, not the builder. In the same way that AWS isn’t responsible for a company building insecure software on their infrastructure, Bubble responsible for ours either.
Bubble knows that it has a large proportion of non-technical users that may assume security is automatic, so it makes sense to put a few simple safeguards in place. However, as app creators, it’s not sufficient to wait around for platform changes - the responsibility for app security ultimately lies with us.
How to make your editor private
It takes about two seconds, and you can do it here:
FAQs
How did you choose which apps to audit?
We used a number of sources including tech stack databases and Bubble itself/marketing materials, but essentially audited any app that we could find, after filtering to remove apps that aren’t live or may be used for templates/instruction (of which there were remarkably few). We do not think there is any reason to believe this sample would not be approximately representative of the ecosystem as a whole.
Does your analysis include test apps?
No. We filtered out any apps that are not deployed to live, and any app with ‘template’ in the app ID.
Could some apps have become insecure after an agency transferred it?
In theory, yes. However, this is exceedingly rare.
Firstly, we used two methodologies to track an editor’s visibility - one that measures it now, and one that measures it when last deployed. The results were similar by both measures. We can reasonably assume that clients that work with agencies don’t deploy live themselves too often, and clients that work with agencies rarely have a reason to make an editor public. Secondly, if clients making apps public were the main driver of public editors in agencies, we’d expect the rate of publicity by agency to be roughly similar. However, there were clear, statistically significant trends with agencies having vastly different numbers of public editors.
If clients did make editors public, these are exceptions that do not materially affect the results.
How do you define which agency built an app?
We defined agency built apps as measured by Bubble in their number of converted apps statistic. If Bubble marked this app as built by Agency X, then we’ve tracked it as so.